-
Killed seven co-workers in Wakefield, Massachusetts massacre
-
Early example of the power of digital evidence
-
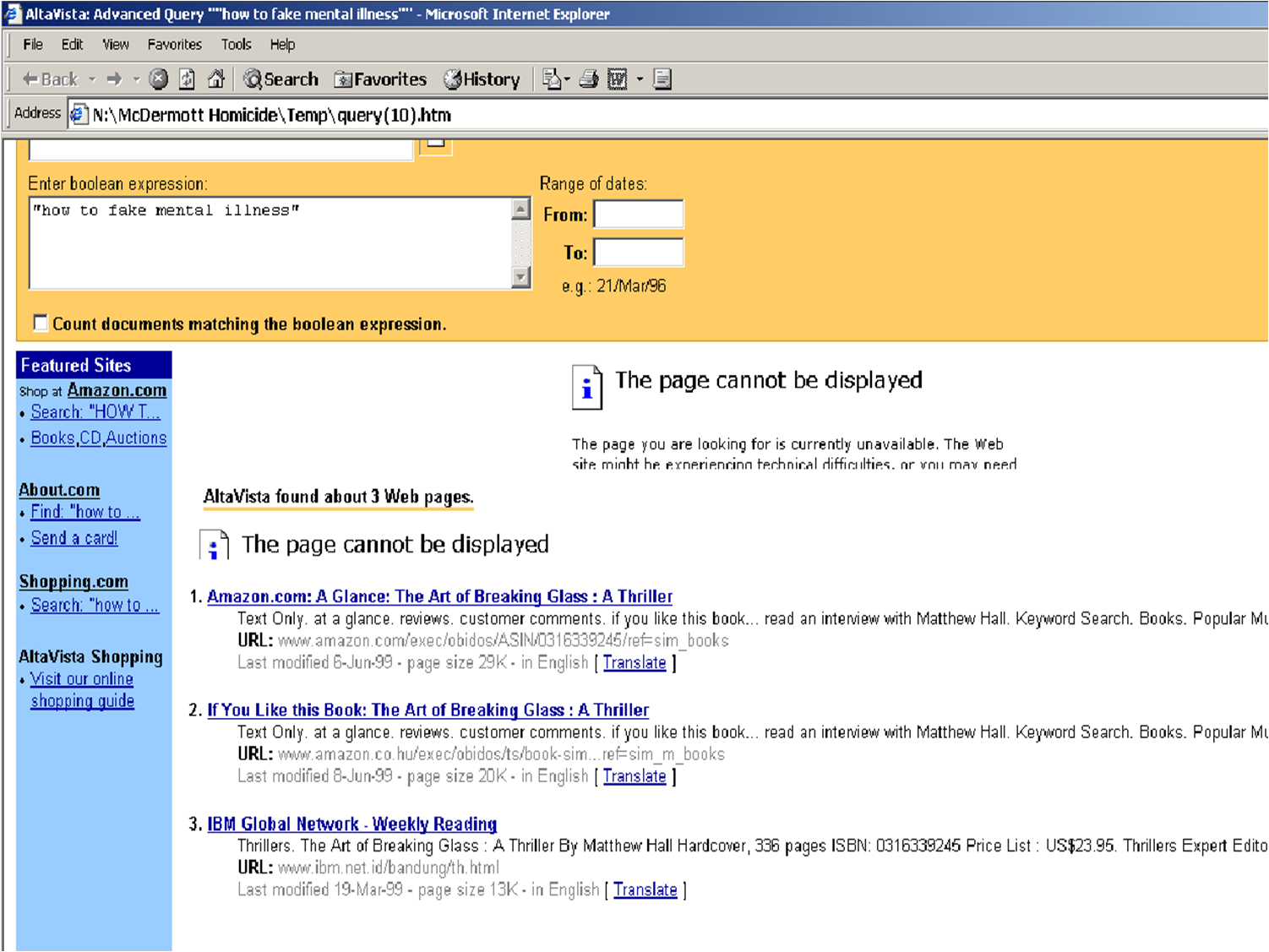
Internet searches related to faking mental illness
-
Convicted and sentenced to life in prison

Course list: http://www.c-jump.com/bcc/
According to FBI, chances of getting caught robbing a bank:
88% -- a cashier starts a day with $3,500
Stealing $$$$ online -- and the chances of getting caught are 11%
London Metropolitan Police has implemented a system to extract mobile phone data from suspects held in custody:
From CNN article "The Internet is a surveillance state"
Quote: "For the first time, Google has confirmed that each year it receives a number of FBI "national security letters," which request that it turn over user account information to the agency. The warrant-less requests are shrouded in secrecy, so the company was able to give publicity only limited number of times it receives and complies with such letters."
"...Although the FBI are capable of doing so, they only monitor people who enter enough keywords to trigger a red flag. And this is a well published fact (just google carnivore software). There simply isn't enough time or resources to monitor the entire US population. Their computers have highly sophisticated algorithms that sort through the endless chatter and if enough key words are triggered, the FBI will take a closer look. But personally, I don't think it is THAT big of a deal. If the government were REALLY that sinister, the whole nation would eventually rise up and rebel against it..."
"...Facebook and Google records only get pulled when they have already taken an interest in you and technically, it has to be through a court subpoena in order to get the rights to that information..."
Focus of a digital investigation is going to be some type of
digital device that has been involved in an incident or crime
there is no single way to conduct an investigation
One approach to use in a digital investigation is based on
the physical crime scene investigation process
If proper preservation procedures of the system being investigated are not followed,
you may accidentally modify data that otherwise could have been evidence
later in a court room you may be accused of destroying exculpatory evidence
Suspect system could delete all files on your system.
It could communicate with a remote system
Preserve the state of the digital crime scene
When important data is saved in a "live" or "dead" system,
the hash should be calculated to show later that the data has not changed.
After original media is preserved, we need to search for evidence
Most of evidence searches are done in a file system and inside files
Use the evidence that has been recovered and determine what events occurred in the system
Reconstruction requires knowledge about the applications and the OS that are installed on the system
A hypotheses is created based on OS/Application capabilities
|

|
On December 26, 2000 McDermott, upset that his employer has garnished his wages due to unpaid taxes, goes to his place of employment, Edgewater Technologies, and proceeds to shoot and kill 7 co-workers on his walk from his desk to the HR department.
McDermott is seated in the company's lobby when Wakefield police officers respond to the 911 calls of the shooting.
He is arrested without incident.
So, how does this involve potential digital evidence?
McDermott was a technically sophisticated individual with an engineering background.
Investigators and prosecutors from the Middlesex DA's Office, along with Wakefield PD recognized the potential for evidence of the planning of the murder may possibly be stored digitally.
They identified several "locations" for potential evidence:
Desktop computers at work and at his residence
PDA with a cradle that synched data with his desktop computer
The user shares of the company's network server belonging to McDermott and all seven victims.
Some connections to justify the search and seizure of these items was:
any/all communications between suspect and victims
Documents relate to the creation of a will as WillMaker software application was found in McDermott's vehicle
An extensive list of keywords produced by investigators and prosecutors containing words specific to the investigation
Recovered content of Web searches on suspect's computer
|
|

|
United States v. Moussaoui

Many tools help investigators analyze a digital system.
Most tools focus on the preservation and searching phases of the investigation.
The Sleuth Kit (TSK) Free tool, www.sleuthkit.org
Encase www.guidancesoftware.com
FTK www.accessdate.com
Prodiscover www.techpathways.com
Smart www.asrdata.com
sourceforge.net/projects/hjt/
HijackThis is a free utility that generates an in-depth report of
registry and file settings on the computer
The following sites have extensive tools and information:
www.e-evidence.info
www.forensics.nl
www.opensourceforensics.org
opensourceforensics.org
www.cftt.nist.gov
www.digital-detective.co.uk/

|
|
Challenge for law enforcement agents, investigators, attorneys, and judges
More challenge: corporate security:


|
|
William Grace and Brandon Wilson
Grace obtains system password while working as an outside consultant to a local police department
break into court computer systems in Riverside, California
alter records relating to previous charges (illegal drugs, weapons, and driving under the influence of alcohol)
altered records indicate that the charges had been dismissed
alter court documents relating to several friends and family members
William Grace and Brandon Wilson
gained unauthorized access to thousands of computers and had the ability to
recall warrants
change court records
dismiss cases
read email of all county employees in most departments, including the Board of Supervisors, Sheriff, and Superior Court judges.
Total of 400 Gbytes of digital evidence was seized.


|
|
Maryland woman named Sharon Lopatka
told her husband she was leaving to visit friends
left a chilling note that caused her husband to inform police that she was missing
police found hundreds of emails between Lopatka and a man named Robert Glass about torture and death fantasies
Lopatka's shallow grave found nearby Glass's trailer in North Carolina, hands and feet tied, strangled
Glass pleded guilty, claiming Lopatka's death was an accident


|
|

|
|

|
|

|
|

|
|
Also found on mobile devices
Links crime, victim, and perpetrator
Reveals how crime was commited
Provides investigative leads
Disproves or supports witness statements
Identifies likely suspects

Electronic and digital evidence
What is digital evidence?
any data stored in electronic form
any data transmitted using a comuter network
text, images, audio, video, program applications installed on a computer

I. Systems made of harddrives, monitors, keyboards, and central units (e.g. laptops/desktops)

II. Communication devices and systems:

|
|
III. Embedded systems. For example,
car computer keeps track of time, speed, brake status, throttle position, prior to an accident (e.g. last 5 seconds of data before the crash.)
arson investigation may rely on data from a microwave oven that was programmed to start a fire at a specific time.

|
|
Rare crimes don't have some computer evidence.
Use of computer and network services effectively provide a behavioral pattern of an individual.
However, digital evidence often:

|
|
Digital Evidence can be altered --

|
|
Digital evidence

can be duplicated exactly
its copy can be examined just like the original
data integrity can be easily verified once properly collected
it is hard to destroy digital evidence:
for example, when file is deleted, the data remains on a disk. Therefore, digital evidence can be successfully recovered using multiple tools and techniques.
Even if offender destroys one copy, another may remain intact (e.g. a backup tape.)

|
|
Criminals often feel safe on the internet, which gives a sense of a virtual world.
However, crime on Internet reflects a crime in real world.
Activity on the web is observable, thus making a criminal vulnerable.

Checks sent by buyers, merchandise never received.
Internet Fraud Complaint Centers receives multiple complaints against the seller.
The seller uses Hotmail account and fake identity.
The seller uses several mail boxes to receive checks from the buyers.
Hotmail logs reveal that the seller uses uunet ISP for most activity.
Uunet is served with subpoena. Uunet discloses suspect's MSN account, home address, phone, and credit card numbers.
One of the banks linked to suspect's credit card is also served a subpoena.
Bank records indicate that buyers checks were deposited to suspect's bank account.
Department of Motor Vehicles provides suspect's photograph.
The photograph is shown to employees at several mail drop locations recognize the suspect.
Credit card company discloses suspect's SSN. The SSN links the suspect to real estate properties.
Finally, computer recovered at one of the properties reveals that it is the place where suspect conducted most of the fraud activity.
In the previous case, without the evidence left on the internet, the activitty would be much harder to trace.
Online auctions reveal thiefs
Search activities reveals names of murderers
CP reveals child abusers
Chat rooms expose local drug dealers
Internet activity reflects criminal activity in real world.
Thus, Internet can be viewed as an extention of the crime scene.
The challenge is to link internet activity with real world events and individuals.
This is often referred to as a following the cybertrail.
Evidence is uncovered in both the phisical world and online.
The cybertrail must be seriously considered even when there is no obvious links to internet activity.
For example, fewer laptops have cable connection, using wireless internet. Therefore, criminal will try to hide the laptop used to access the internet. Such laptop will reveal suspects ISP and online identity.
Another ebay fraud example:

Great source of information, often more consistent than a home computer.
Rich source of email, chat, newsgroup activity, and access to websites.
Many corporate networks record all network activity and store it for prolong periods of time.
It is also easier to identify relevant pieces of data on a smaller network rather than on the Internet.
Very useful info comes from dates/times of logins in and out of the computer and network domain.

Network anonymity makes it difficult to attribute findings to a particular individual

Often is volatile, therefore communication has to be intercepted as it occurs.
May span cities, networks, and multiple countries.
Different locations will have different local time, creating additional barriers for timeline assembly.
Lost evidence may be impossible to recover.
reconstruct crime
identify suspects and victims
recreate the timeline of events
understand the motivations of criminals

Forensic Science provides:
proven investigative techniques
similar to shoe prints, associated with the shoes that left the prints, computer forensics helps to reconstruct a crime and generates additional leads in investigation.
Being forensic means
being suitable for an admission in a court of law
being able to persuade based upon proof

Research history of computer crime investigation. Write a 1.5 page paper by answering the following questions:
In your opinion, what is the earliest computer crime ever commited?
Which Florida Act enacted in 1978 was related to computer fraud and intrusion? Hint: Flagler Dog Track.
What is US Federal Computer Fraud and Abuse Act and when it was passed/amended?
When was UK Computer Abuse Act passed in Britain?
What was Operation Long Arm in 1992?
What was Communications Decency Act (CDA) in 1996?
What was Child Online Protection Act (COPA) in 1998?
To submit your document, go to CIT-155 online website. You should have already received your login and password for this website. If not, then email me at
and I will reply back with your access credentials.
On the Main Menu, follow the link to Submit Homework, select Assignment a1, and upload your file.
Note: the system will display an 8-digit confirmation number once the file is successfully uploaded. You can save the confirmation number for your own records, but this is not a required step and no further actions are needed on your part.
Let me know if you are experiencing any problems, otherwise -- good luck on your first assignment!