Course list http://www.c-jump.com/bcc/

Forensic examiners pass their work on to prosecutors (or other decision makers) who
scrutinize the findings, and
decide whether to continue or refocus to solving other matters.
In the case of the courts:
investigators present findings to the trier-of-fact(*)
Jury decides if the merits of the evidence make a strong enough case to proceed to trial.
_________________
(*) A trier of fact (or finder of fact) is a person or group who determines facts in a legal proceeding. In a jury trial, the jury is the trier of fact. The jury finds the facts and applies them to the law it is instructed by the judge to use in order to reach its verdict.
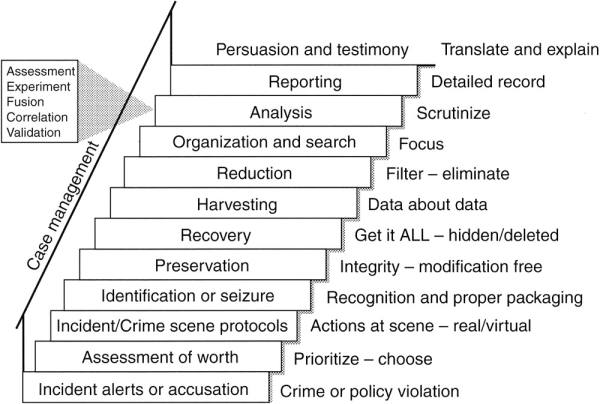
A place where an event takes place:
...a citizen reporting possible criminal activity
...an alarm from an intrusion detection system
...a system administrator reviewing firewall logs
...curious log entries on a web server, and so on.
Investigative personnel is dispatched to a physical scene
The prevalence of computers makes it increasingly likely that even traditional crimes will have related information derived from digital sources that require close scrutiny.
Consider the source and reliability of the information:
An individual making a harassment complaint of repeated offensive messages might actually a computer virus.
A network intrusion detection system (IDS) alert may simply indicate an attempted, but unsuccessful intrusion attempt.
Both of the above are false alarms.
Additionally, starting detailed investigation prematurely -- without proper authorization or protocols, can undermine the entire process.
An effort should be made to perform only the minimum actions necessary to determine if further investigation is warranted.
All suspected criminal activity must be investigated.
In civil, business, and military operations, suspicious activity is investigated but corporate policy and continuity of operations often replaces legalities.
First challenge: retain and document the state and integrity of items (digital or otherwise) at the crime scene.
Protocols and procedures are employed at this critical juncture to minimize the chance of errors, oversights, or injuries.
Whoever is responsible for securing a crime scene -- whether first responders or digital evidence examiners -- should be trained to follow accepted protocols.
Preventing people from disturbing a single computer or room is relatively straightforward.
If networking involves multiple locations, securing those presents additional challenge.
Once the scene is secured, potential evidence of an alleged crime or incident must be seized.
It is necessary to record details about each piece of seized evidence:
by doing this, the evidence authenticity is established and chain of custody is initiated.
For instance, numbering items, photographing them from various angles, recording serial numbers, and documenting who handled the evidence.
The goal is to keep track of where each piece of evidence came from and where it went after collection.
Do not change data held on a computer or other media that may subsequently be relied upon in court.
Chain of custody must be created and preserved; An independent third party should be able to examine collection processes and achieve the same result.
See Electronic Crime Scene Investigation: A Guide for First Responders (USDOJ 2001).
Standard operating procedure (SOP) covers simple investigations involving a few computers.
SOP is necessary to
avoid mistakes,
ensure that best available methods are used,
increase the probability that two forensic examiners will reach the same conclusions when they examine the evidence.
First, the original material is cataloged and stored in a proper environmentally controlled location, in an unmodified state.
Second, an exact copy of the original material is made and later used in examination.
Duplicate copies of all sources of digital data are made.
In practice, this is where digital forensics begins!
Next, ensure the integrity of potential evidence, both physical and digital.
Accuracy and reliability, as well as professional acceptance of tools used, may be subject to question by opposing council if the case is prosecuted.
This stage involves extracting data that has been
deleted,
hidden,
camouflaged,
otherwise unavailable for viewing while using the native operating system and resident file system.
Recovery process is performed on copies of original digital evidence from the preservation step
none NOTE: this may not be possible in the case of embedded systems.
The objective is to identify, and if possible make visible, all data that can be recognized as belonging to a particular data type.
This effort provides the most complete data timeline and may provide insight into the offender's motives.
At this stage the investigator classifies all recovered data.
Result is harvested data for later analysis: the data is logically organized into groups with certain class characteristics.
Each data group will be related to major known facts at this point of the investigation.
For example, an accusation related to printing counterfeit money requires visual digital evidence most likely rendered in an enhanced resolution computer graphics formats like BMP, TIFF, and PDF.
Therefore, the investigators would likely be looking for the existence of files exhibiting characteristics from these graphic formats.
The goal is both eliminate irrelevant, as well as set focus on specific data items that are potentially critical to the investigation.
The decision to eliminate or retain is made based on external data attributes, such as
hashing or checksums
type of data (after the type is verified.)
The criteria used to eliminate certain data are very important since it might possibly be questioned by judge, jury, or any other authorized decision maker.
A searchable index of the data is created to enable efficient review of the found materials.
The index helps identify relevant, irrelevant, and otherwise privileged material.
Any tools or technology used in this regard should be understood fully and the operation should follow as many accepted standards as exist.
Detailed scrutiny of data!
Review and study of specific, internal attributes of the data.
Interpret text and any other readable data
Understand formats of binary images/audio/video data items.
Establish logical links, determine the source of items, and ultimately locate the offender.
Experimentation leads to falsification or general acceptance. Therefore,
All experimentation techniques must be documented rigorously so that the community, as well as the courts, have the opportunity to test them.
Validation is the output of the analysis stage.
Proposed findings are submitted to jurists or other decision makers as proof positive for prosecution or acquittal.
Objectivity is vital to your reputation and can lead to false conclusions and personal liability!
LISER v. SMITH, 2003:
54-year-old hotel waitress was killed.
Investigators obtained a photograph of Jason Liser from a bank ATM where the victim's bank card had been used.
Investigators thought they have found the killer -- Jason Liser.
Bank manager expressed warning that there could be a discrepancy between the time indicated on the surveillance tape and the actual time.
Liser's photograph was publicized and he was subsequently arrested.
Liser denied any involvement in the murder.
Liser's bank statement confirmed that he had been at the ATM earlier that night, and used his girlfriend's bank card, not the murder victim's.
Investigators made an experimental withdrawal from the ATM and found that the time was significantly inaccurate.
That proved Liser had used the ATM before the murder took place.
Eventually, information relating to the use of the victim's credit card several days after her death implicated two other men who were convicted for the murder.
Liser sued the District of Columbia and Jeffrey Smith, the detective responsible for the mistaken arrest, for
false arrest and imprisonment,
libel and slander,
negligence, and
providing false information to support the arrest.
The court dismissed all counts except the negligence charge.
The court felt that Smith should have made a greater effort to determine how the bank surveillance cameras operated or consulted with someone experienced with this type of evidence noting.
Liser's other lawsuit against Bank of America for negligence and infliction of emotional distress due to the inaccuracy in the timing mechanism was dismissed.
Fundamental concepts such as Locard's Exchange Principle, class and individuating characteristics of evidence, and establishing continuity of offense are very important.
The ultimate aim of investigative is to help investigators and examiners ascend a sequence of steps that are
generally accepted,
reliable,
repeatable,
lead to logical, well documented conclusions of high integrity.
Anyone responding to an accusation or incident should already have policies and protocols to follow and should have the knowledge and training to follow them.